It’s no coincidence that Graylog 6.1 is making its debut right before Halloween. This release is a true behemoth, designed to tackle some of the longest-standing and most challenging issues in Security Event and Information Management (SIEM). Packed with innovations, Graylog 6.1 is here to change the game.
1. Getting to the Alerts that Matter
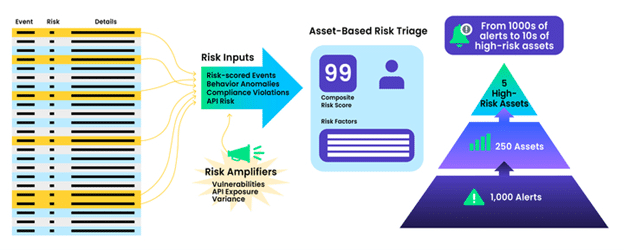
In the world of SIEM, finding the alerts that truly matter is a daunting task. With Graylog 6.1, we introduce Asset Risk Prioritization, a groundbreaking feature that triangulates corroborating sets of activities targeting the same user or device. This allows us to identify the systems or users with the highest probability of compromise. Instead of experiencing alert fatigue manually triaging individual alerts, our focus on assets radically reduces the number of things to triage. It gives analysts a cheat code by starting their investigation with a set of evidence.
2. Maximizing the Value of Your Data
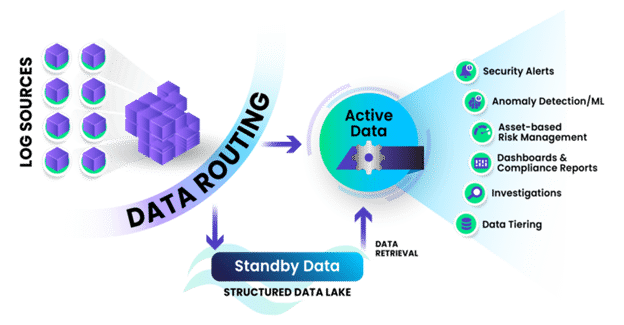
The sheer volume of data in SIEM can be overwhelming, with much of it never making it into analytics or investigations. Graylog 6.1 introduces Data Routing, giving customers the power to manage this data deluge without compromise. You can now collect data and park it in a standby data lake to be retrieved if necessary. You can chose to only pay for the data that adds value to your real-time analytics, dashboards, and investigations.
3. Visualizing Threat Detection Coverage
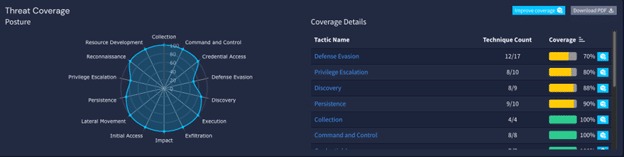
Understanding how your SIEM aligns with threat detection is crucial. Graylog 6.1 offers a visual map of your threat detection coverage. Coverage that’s constantly updating as new Illuminate content becomes available to help you shore up your defense mapped to the MITRE ATT&CK framework. This dynamic tool ensures your security measures are always up-to-date taking advantage of what your Illuminate content feed has to offer.
4. Streamlining Investigations with AI
While others seem to have bet their Marketing dollar on AI, we are judiciously leveraging large language models where they make the most sense – summarization.

Previously, we introduced remediation steps embedding a course of action directly into event definitions. Now, 6.1 adds the ability to use GenAI to identify connections within the evidence you’ve gathered in your investigations. In Graylog 6.1, AI Investigation Summary analyzes events, assesses impacts, and offers dynamic recommendations to guide analysts through investigations. And it simplifies the creation of incident response reports for stakeholders.
A New Era for SIEM
Graylog 6.1 is not just another update. It’s a comprehensive solution to some of the most pressing challenges in the industry. By addressing alert fatigue, maximizing data value, visualizing threat coverage, and streamlining investigations, Graylog 6.1 is set to empower organizations to achieve their security objectives. Get started today by upgrading your current cluster, or if you are not a current customer see a demo of it in action. We’re thrilled to bring this monster of a release to the community and can’t wait to hear your feedback!

The post Introducing Graylog 6.1: A Monster Release Just in Time for Halloween appeared first on Graylog.